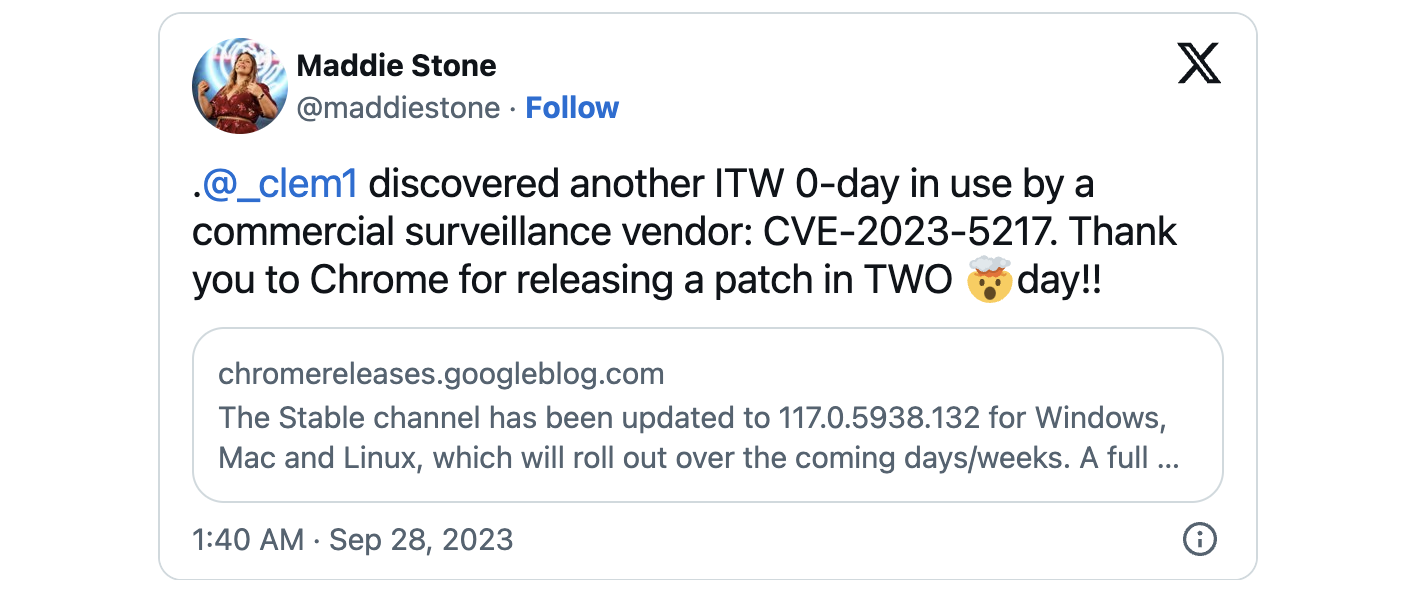
Google patched the fifth Chrome zero-day vulnerability used in attacks since the beginning of the year in emergency security updates released today.
“Google is aware that an exploit for CVE-2023-5217 is widely available,” the company said in a security advisory published Wednesday.
This vulnerability is fixed in Google Chrome version 117.0.5938.132, which is available on the Stable Desktop channel to Windows, Mac and Linux users worldwide. Although the message said it would likely take days or weeks for the patched version to reach the entire user base, the update was available immediately when BleepingComputer checked for updates.
The web browser will also automatically check for new updates and install them automatically the next time you start it.
Used for spyware attacks
The high-level zero-day vulnerability (CVE-2023-5217) is caused by a stack buffer overflow flaw in the VP8 encoding of the open source libvpx video codec library; This flaw has an impact ranging from application crashes to arbitrary code execution. .
The bug was reported by Google Threat Analysis Group (TAG) security researcher Clement Lessin on Monday, September 25.
Google TAG researchers are known for frequently detecting and reporting the use of zero-days in targeted spyware attacks by state-sponsored threat actors and hacker groups targeting high-risk individuals such as journalists and opposition politicians.
Today, Google TAG’s Maddy Stone discovered that the CVE-2023-5217 zero-day vulnerability is being used to install spyware.
Google TAG, along with Citizen Lab researchers, also disclosed on Friday that three zero-day patches, patched by Apple last Thursday, were used to install the Cytrox Predator spyware between May and September 2023.
Although Google said today that the CVE-2023-5217 zero-day was used in the attacks, the company has not yet provided further information about the incidents.
“Access to error details and links may be limited until most users update the fix,” Google said. “We will also maintain restrictions if the bug exists in a third-party library that other projects depend on but have not yet fixed.”
As a direct result, Google Chrome users will have plenty of time to update their browsers as a preventative measure against possible attacks.
This proactive approach can help reduce the risk of threat actors creating their own exploits and exploiting them in real-world scenarios, especially as more technical details emerge. Two weeks ago, Google released another zero-day exploit (tracked as CVE-2023-4863), the fourth since the beginning of the year.
Originally flagged as a flaw in Chrome, the company later assigned another CVE (CVE-2023-5129) with a maximum severity rating of 10/10; which flagged this as a critical vulnerability in libwebp (a library used by many projects). Signal, 1Password, Mozilla Firefox, Microsoft Edge, Apple’s Safari, and Android’s native web browser). Source