Abuse: Ivanti leak infects networks worldwide
- January 25, 2024
- 0
Of the 26,000 devices visible online, 492 Ivanti VPN devices have now been hacked. Germany, Italy and the Netherlands make up the top three in Europe. The security
Of the 26,000 devices visible online, 492 Ivanti VPN devices have now been hacked. Germany, Italy and the Netherlands make up the top three in Europe. The security


Of the 26,000 devices visible online, 492 Ivanti VPN devices have now been hacked. Germany, Italy and the Netherlands make up the top three in Europe.
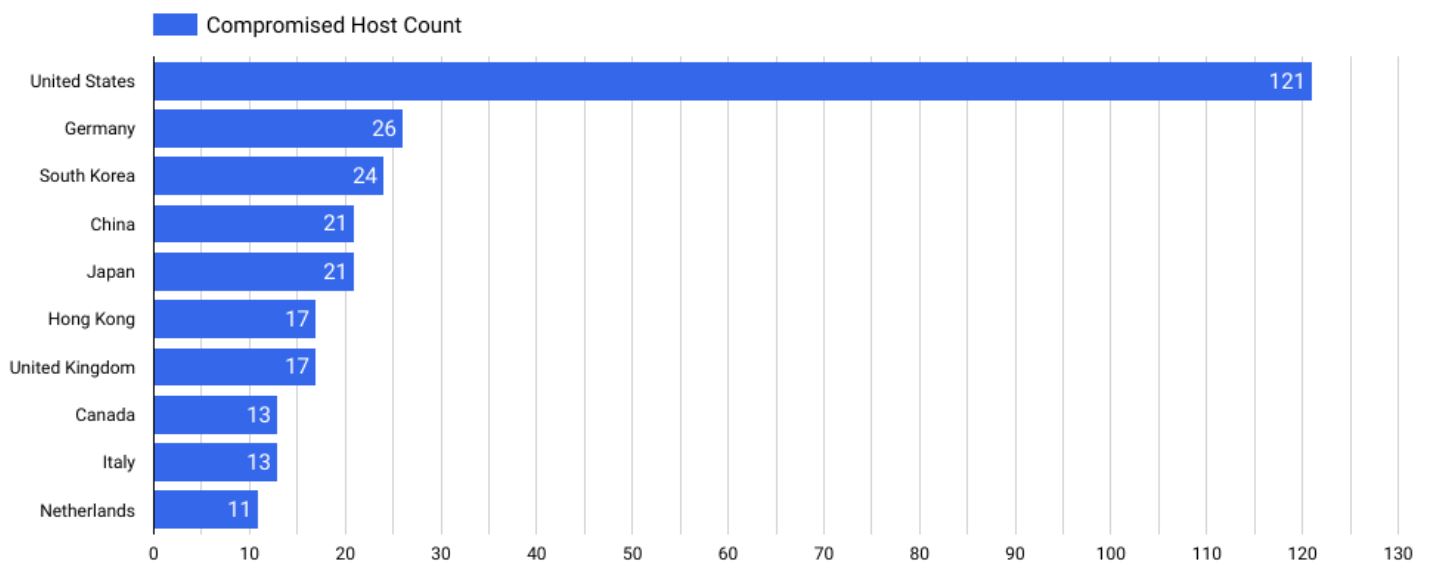
The security company Censys writes that hackers with ties to the Chinese government are massively exploiting two vulnerabilities in Ivanti devices to gain access to VPN devices. As of Tuesday afternoon, 492 VPN devices had already been hacked, more than a quarter of them in the USA.
In Europe, Germany in particular is likely to be concerned about 26 hijacked aircraft. Italy (13) and the Netherlands (11) complete the top three in Europe and the top 10 worldwide.
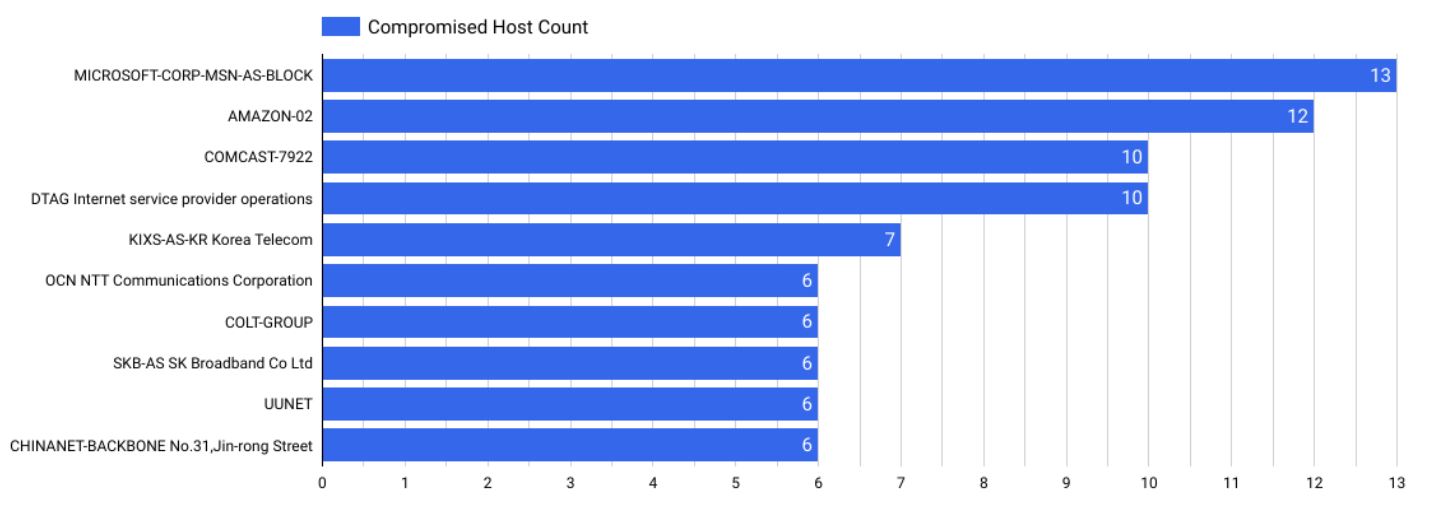
If you look at the hyperscalers’ cloud services, Microsoft Azure (13) and AWS (12) are at the top when it comes to infected devices.
“We ran a secondary scan on all Ivanti Connect Secure servers in our dataset and found 412 unique hosts with this backdoor,” Censys researchers write. “In addition, we found 22 different ‘variants’ (or unique recall methods) that could indicate multiple attackers or a single attacker evolving their tactics.”
VPNs are an ideal device for hackers to infect. They are almost always active and are located at the edge of the network where incoming connections are allowed. Because VPNs communicate with large portions of the internal network, hackers can work to further infiltrate.
All versions of Ivanti Connect Secure (ICS), formerly known as Pulse Secure, are affected by the two vulnerabilities. For example, Ivanti warned earlier this week that administrators will not be allowed to deploy new device configurations to devices after applying the patch.
“Customers should stop pushing configurations to appliances when XML is present and should not continue pushing configurations until the appliance is patched,” Ivanti said in a new update released Saturday.
“If the configuration is pushed to the device, some key web services will stop working and mitigation will stop. This only applies to customers transferring configurations to devices, including configuration transfers via Pulse One or nSA. This can occur regardless of a full or partial configuration push.”
26,000 unique Connect Secure hosts are publicly visible on the Internet and have software containing the two vulnerabilities. You can read here how you can temporarily solve the problem today while you wait for a patch.
Source: IT Daily
As an experienced journalist and author, Mary has been reporting on the latest news and trends for over 5 years. With a passion for uncovering the stories behind the headlines, Mary has earned a reputation as a trusted voice in the world of journalism. Her writing style is insightful, engaging and thought-provoking, as she takes a deep dive into the most pressing issues of our time.