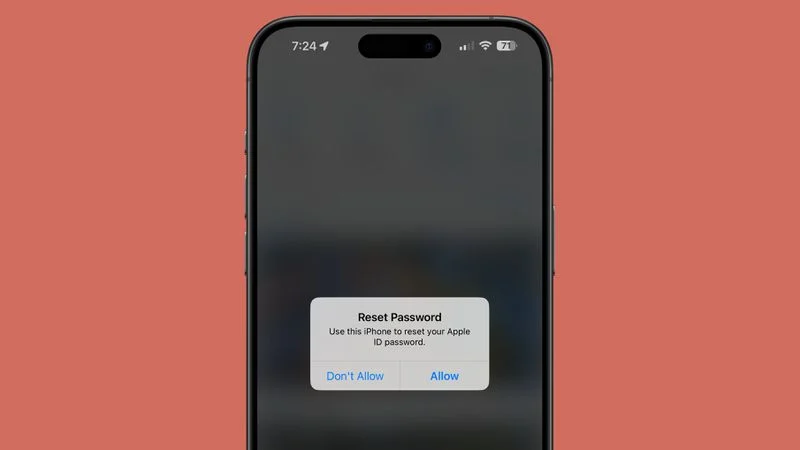
According to KrebsOnSecurity’s reportPhishing attacks using what appears to be a bug in Apple’s password reset feature are becoming more common. Many Apple users have been the target of an attack that bombards them with endless notifications or multi-factor authentication (MFA) messages in an attempt to get them to confirm an Apple ID password change.
An attacker can force a target’s iPhone, Apple Watch, or Mac to repeatedly display system-level password change confirmation texts, hoping that the target will accidentally approve the request or get bored with the notifications and click accept. If the request is approved, the attacker can change the “Apple ID” password and lock the Apple user out of his account.
Since password requests are directed to “Apple ID”, they appear on all the user’s devices. Thanks to notifications, all connected Apple products cannot be used without closing pop-ups on each device one by one. Twitter user Parth Patel, who recently shared his experience of being the target of an attack, said that he was unable to use his devices until he clicked “Block” to receive more than 100 alerts.
When attackers can’t get someone to click “Allow” on a password change notification, targets often receive phone calls that appear to be from Apple. In these calls, the attacker claims to know that the victim is under attack and attempts to obtain the one-time password sent to the user’s phone number while attempting to change the password.
In Patel’s case, the attacker used information obtained from a person-finding website, including his name, current address, past address and phone number, to give the person trying to access his account enough information to work. The attacker misunderstood his name and became suspicious because he was asked for a single-use code. Apple was clearly sending this with a message confirming that Apple does not want these codes.
The attack appears to be related to the attacker having access to the email address and phone number associated with the “Apple ID”.
KrebsOnSecurity He investigated the issue and found that attackers were using Apple’s page to retrieve a forgotten “Apple ID” password. This page requires an “Apple ID” email or phone number and has a CAPTCHA. When an email address is entered, the page displays the last two digits of the phone number associated with the Apple account, and a system alert is sent when the missing digits are entered and clicked Submit.
It’s unclear how the attackers exploited the system to send multiple messages to Apple users, but this appears to be a bug they exploited. It’s unlikely that Apple’s system was designed to send more than 100 requests, so the rate limit was probably bypassed.
Owners of Apple devices targeted by this attack should click Decline on all requests and be aware that Apple does not ask for a one-time password reset code.