Confidential Computing: Where do we stand in protecting sensitive data?
- July 24, 2024
- 0
Several security techniques help protect data at rest and in transit from point A to point B. But what about the data in use? What techniques are there
Several security techniques help protect data at rest and in transit from point A to point B. But what about the data in use? What techniques are there


Several security techniques help protect data at rest and in transit from point A to point B. But what about the data in use? What techniques are there and how secure are they?
Confidential computing promises better protection of sensitive data at the time of processing. Over time, three different techniques have been developed to protect large customer data sets: Homomorphic Encryption (HE), Secure Multiparty Computation (MPC), and Trusted Execution Environments (TEE). These confidentiality techniques each use a different technology to protect data in a secure manner.
What can these techniques do, how mature are they, and in what form are they being brought to market by chip designers such as Intel, AMD, and AWS? Fabien Petitcolas, cybersecurity researcher at Smals, provides more information on these techniques in a webinar attended by our editors.
Homomorphic encryption (HE) is an encryption method in which data is sent encrypted without unlocking it. In this form of encryption, the ciphertexts are transformed according to the desired calculation and then sent back to the client, who can then decrypt the result using a key.
This form of encryption is particularly interesting for extremely sensitive information, such as medical or financial data. It offers a high level of data protection, as the data is never made accessible (to the processor) in its unencrypted form during processing.
Secure Multiparty Computation (MPC) works very differently from HE. In MPC, both data and computing power are shared. This technology allows multiple parties to perform calculations together, but each party’s inputs remain secret to each other. The result of the calculations is known only to the designated parties.
Like HE, MPC is based on a strong theoretical foundation, based on four decades of scientific research, and is commonly used in research institutes. “For example, KULeuven has strong domain expertise,” says Petitcolas. Despite the strong theoretical foundation, there are only a limited number of practical applications today. The complexity of commissioning and managing such a technology, combined with the high communication costs between the parties, means that MPC is not yet generally applicable.
A third approach to protecting data is Trusted Execution Environments (TEE). Maximum security is sought on the hardware. This technology is based on the idea that a system cannot be secure if the lowest layer, in this case the hardware, is not secure.
With TEE, you rely entirely on the hardware manufacturer, not the infrastructure. You must trust that the hardware manufacturer has implemented TEE correctly for optimal security.
How advanced are these security technologies now? The following graphic shows the maturity level of the three different encryption technologies. The techniques are ranked on a maturity scale from “new” to “best”. The vertical axis shows the value within the value chain, from low to high. “This view shows that HE and MPC are less mature compared to TEE and are limited to niche applications,” says Petitcolas.
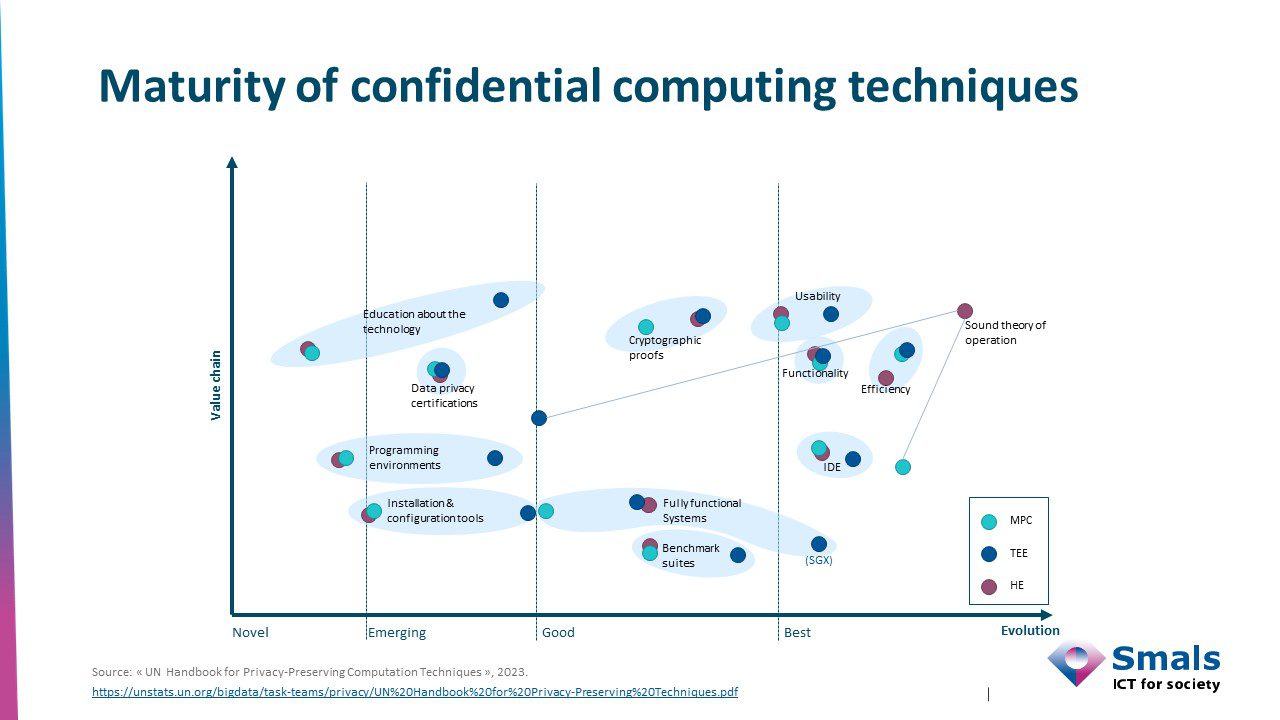
The main players in the confidential computing space include chip manufacturers (e.g. Intel and AMD) and large computing infrastructure providers (e.g. Microsoft, Google and AWS). Each has its own approach but the same goal: to meet the needs of customers who handle sensitive information.
AMD and Intel are the two main developers of microprocessors that provide the necessary functionality for confidential computing in large data centers. While Intel’s TDX and AMD’s SEV-SNP technologies are designed to protect entire virtual machines, SGX technology is quite different and has a smaller attack surface.
In recent years, Intel SGX has been subjected to regular attacks. We may wonder if this security technology is completely watertight, but it is certainly secure.
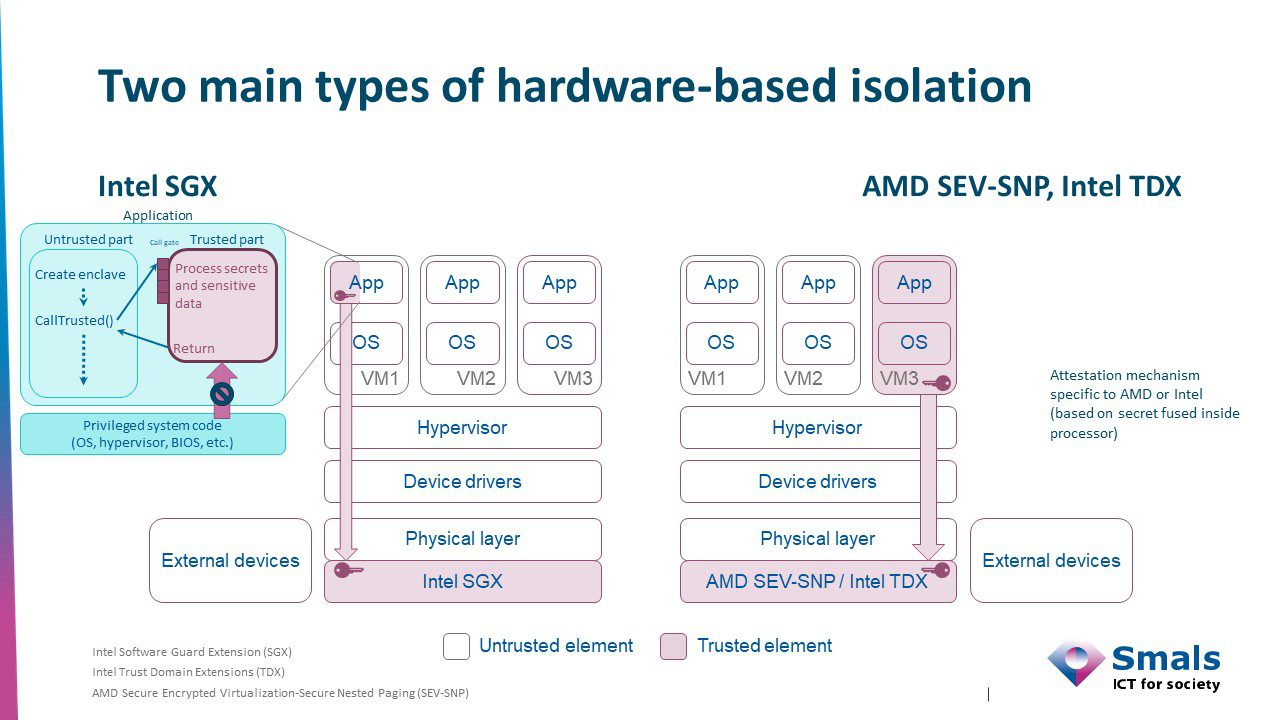
Finally, AWS defines confidential computing as the use of specialized hardware and associated firmware to protect customer code and data from outside access during processing.
Amazon places emphasis on the architecture of the Nitro system rather than on the availability of a specific microprocessor to provide a TEE. However, since April 2023, AWS also offers the ability to create EC2 instances using AMD’s SEV-SNP technology.
Although there are various security technologies and manufacturers also have a wide range of offerings, there is still a problem of trust. “The customer is heavily dependent on the infrastructure provider and the relationship is based heavily on trust,” says Petitcolas. In addition, there is still uncertainty about the performance characteristics due to the increased complexity.
Source: IT Daily
As an experienced journalist and author, Mary has been reporting on the latest news and trends for over 5 years. With a passion for uncovering the stories behind the headlines, Mary has earned a reputation as a trusted voice in the world of journalism. Her writing style is insightful, engaging and thought-provoking, as she takes a deep dive into the most pressing issues of our time.