XDR for SMEs: What is it and why do you need it?
- September 12, 2024
- 0
An XDR solution for SMBs that allows you to continuously monitor an IT environment for cyber threats at an affordable price? Yes, why not? To be better protected
An XDR solution for SMBs that allows you to continuously monitor an IT environment for cyber threats at an affordable price? Yes, why not? To be better protected


An XDR solution for SMBs that allows you to continuously monitor an IT environment for cyber threats at an affordable price? Yes, why not?
To be better protected against cyberattacks or data leaks, it is important that companies continuously monitor their IT environment and detect and resolve potential threats in a timely manner. However, IT teams often have their hands full with other tasks or lack the budget to set up a dedicated SOC team.
For this reason, a SOC (security operation center) team is often brought in to continuously monitor threats from multiple angles. Such solutions are widely used in large enterprises, but may not seem like an obvious choice for SMBs due to the high cost. As a small business, how can you implement a comprehensive security solution without breaking your budget?
There are several buzzwords for a Security Operation Center (SOC), including a well-known concept in the security landscape: Managed Detection and Response (MDR). These terms refer to the continuous monitoring of security events, such as a firewall, antivirus, or spam. With all these security notifications and alerts, IT teams still need to see the forest for the trees. To know when to respond and when not to, the SOC team needs a central point where all reports converge.
An XDR or SIEM solution can ensure this. XDR, or Advanced detection and responsecollects data from all endpoints and logs of other security events, such as firewall activities, and bundles them in a central dashboard. SIEM stands for Security information and incident managementt and goes a little beyond the pure security component. “With a SIEM solution, you can also monitor users for abnormalities, e.g. failed logosChanges made by users who should not have rights to them, or a ActiveDirectory (AD),” says Robin Bruynseels, cybersecurity and SOC engineer at Easi.
Another big difference from a SIEM solution is that it also contains raw logs. This is data that may not be of much use to you right away. XDR is mainly about detecting real products, like an anti-virus or anti-spam program, that detect something. “XDR is a more filtered version of SIEM that also detects things that are not always of use to your security team and can also react quickly when needed,” says Bruynseels.
Security solutions such as XDR or SIEM are often used in large companies that have the resources and knowledge to build their own SOC team or work with an external, specialized team. “We have an ‘Easi SOC Pro module’ that is designed for large companies with more than a thousand users. However, such SIEM solutions are unaffordable for small SMEs,” says Bruyneels.
We also want to offer small, growing companies an affordable product that does the same thing as a SIEM solution, but with slightly fewer features.
Robin Bruynseels, Cybersecurity and SOC Engineer at Easi
But small businesses also need a comprehensive security solution that connects all endpoints. “To fill the gap in the market and offer SMEs a similar security product, we at Easi have created a SOC module specifically for SMEs,” says Bruynseels.
This new module tailored to SMEs was called “Bluehorn”. The product was developed entirely in-house by an Easi security engineering expert. “He developed his own security product that offers an affordable and comprehensive security solution for SMEs,” says Bruynseels. It thus serves as an alternative to a SIEM solution, but tailored to SMEs. To be clear: Bluehorn is the product, behind it you still need Easi’s SOC team to perform the analytics on the application.
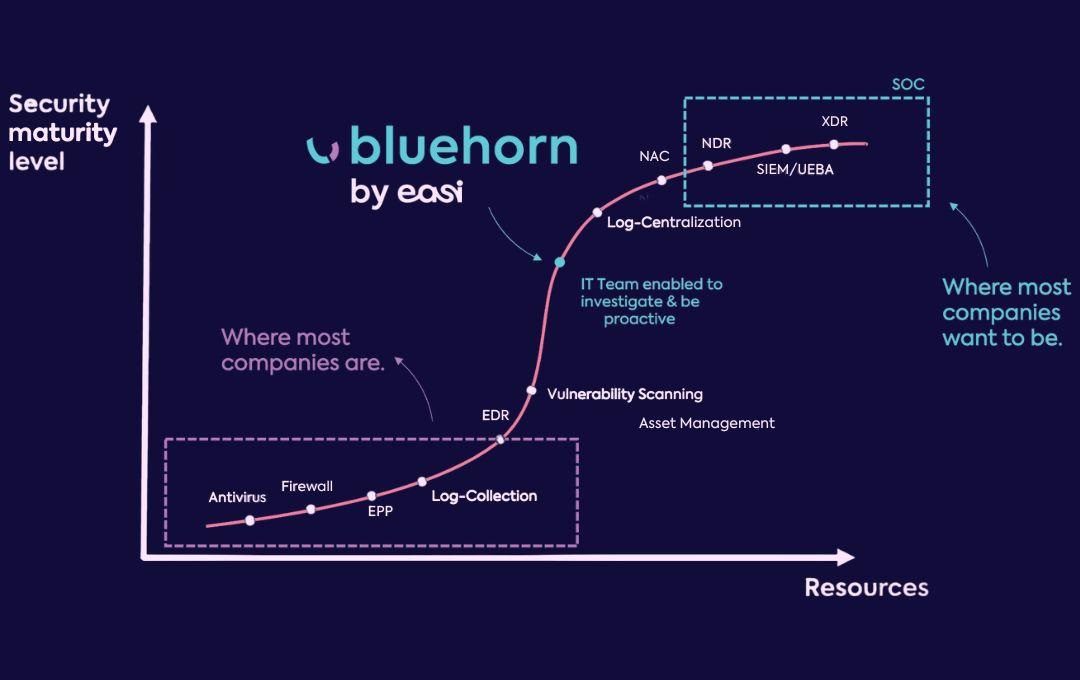
Bruynseels: “The advantage of having your own product is that you can determine the capabilities yourself and add new features.” Easi also has a lot of internal knowledge in the field of security, so the product can be continuously adapted based on experience and expertise.
“Originally, Bluehorn was a kind of asset management tool. As we noticed that the security aspect has more interest and need, we switched to the XDR principle,” says Bruynseels. Easi wants to bring all security components together to respond from one point of view. “If someone logs in from China, Bluehorn will indicate that this is not normal behavior and we from the SOC team can immediately remove that user’s access.” So it’s not just ‘advanced detection‘, but also ‘Answer’.
Bluehorn is a flexible product. “We rely on certain products that are already integrated into our security solution. If customers work with other software or, for example, a specific firewall that is not included in Bluehorn, we can ensure that the integration takes place,” explains Bruynseels. The aim is for the platform to evolve together with the customer.
Bluehorn is continually evolving, but there is no intention to compete with enterprise products.
Robin Bruynseels, Cybersecurity and SOC Engineer at Easi
Bluehorn comes in a box, nothing more, nothing less. “When we introduce new features, customers can just use them and don’t have to pay any extra costs,” says Bruynseels. “We can also learn from customers’ products. That way it grows together with the customer and we can provide our product with multiple capacities. It’s constantly evolving.”
While other SOC providers look at the number of protocols when determining pricing, Easi does not. “We calculate the price based on the number of assets: how many PCs, laptops and servers the IT environment has,” explains Bruynseels.
Nevertheless, this investment remains a big step for medium-sized companies. Bruynseels: “Normally, small companies are interested in such security solutions, but they do not have this investment in their financial goals, for example.”
Given the whole NIS2 story, companies will see this differently in the future. NIS2 will play an important role in this, as it is now also important for SMEs. “It creates more awareness of the security story,” says Bruynseels.
“Above all, we want to help IT teams increase their maturity in the area of cybersecurity. “Our product develops together with the customer into a comprehensive cybersecurity solution, tailored to the SME,” concludes Bruynseels.
Source: IT Daily
As an experienced journalist and author, Mary has been reporting on the latest news and trends for over 5 years. With a passion for uncovering the stories behind the headlines, Mary has earned a reputation as a trusted voice in the world of journalism. Her writing style is insightful, engaging and thought-provoking, as she takes a deep dive into the most pressing issues of our time.