Although when we talk about Windows attacks, the focus is usually on phishing, ransomware, etc. brute force attacks are still a very common techniqueand that under the right circumstances it can be extremely effective, much to the dismay of users who are victims of attacks in which it is used.
Even if you don’t know the essence of this technique, you can certainly get a fairly accurate idea of what it consists of from its name, and you won’t be wrong. Brute force is try passwords and other passwords in turn until, if the attacker is lucky, he finds the right one. This can be done on its own or by relying on so-called dictionaries, which are nothing more than huge databases of keys, or patterns for them, that are usually used in creating passwords.
Brute force attacks are of course automated, password-detection software will chain each test to the next as fast as the compromised system will allow. In other words, we’re not talking about a person manually entering every possible password, but a development capable of testing thousands of potential keys per minute.
Sometimes dictionaries in addition can be combined with the victim’s knowledgeall the knowledge known about him (from his date of birth to his pet’s name) can be taken into account when creating a list of possible passwords to subsequently launch an attack.
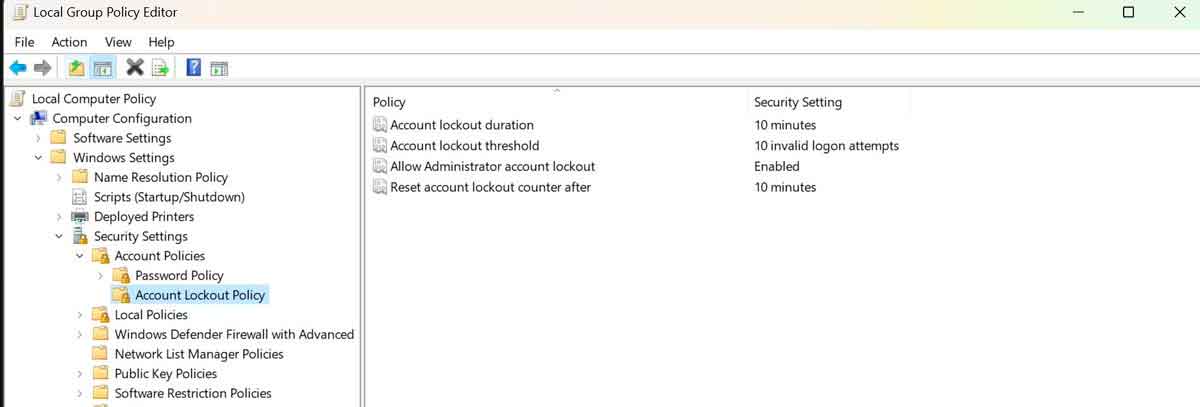
Windows in all its flavors are one of the usual victims of brute force attacks, but Microsoft seems to have had enough of this circumstance and as we can see in this tweet From David Weston, vice president of enterprise security and operating system security at Microsoft, Microsoft began adding default account policies in Windows 11 to substantially mitigate the risks of brute force attacks.
This new policy, which will also come to Windows 10 (although in this case it will not be activated by default), allows you to set a maximum number of failed attempts due to a bad password and once reached, retesting will be blocked for a period of time that we determine. By default it will be 10 attempts followed by 10 minutes of blocking. So with this default setting, we reduce the maximum number of tests that can be run in an attack to just 60 per hour, when under other circumstances the number is infinitely higher.
