Vulnerabilities present in Intel, AMD processors and even ARM have become so commonplace that it’s no longer surprising to see researchers discover and publish new security flaws that often can’t be fixed, leaving you to pile on patches in microcode, kernels, drivers, and applications. to minimize the attack surface.
If this entry has been published, it is because new vulnerabilities have been found again, this time affecting Intel and AMD processors. However, the vulnerabilities are different, so a vulnerability affecting Intel affects only Intel and a vulnerability affecting AMD affects only AMD.
ÆPIC, a new vulnerability capable of exposing confidential data that affects Intel
We’ll start with a security flaw discovered in Intel processors that was given a name ÆPIC. According to the researchers, this is the first CPU-level flaw that can architecturally expose sensitive data. It resides in the Advanced Configuration and Power Interface (ACPI) and is used through memory-mapped input/output (MMIO).. In case it wasn’t clear, this is not a variant of Specter exploited via a side-channel attack.
If a malicious actor manages to successfully exploit ÆPIC, which requires administrative rights, he will be able to obtain encryption keys and other sensitive data that are allegedly protected by Software Guard Extensions (SGX), a technology introduced by Intel in its modern processors with with the aim of limiting the possible success paths of cyber attacks.
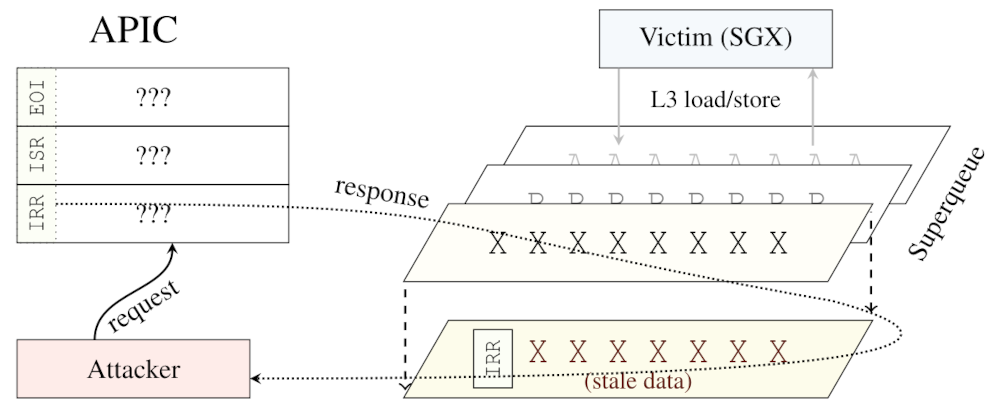
SGX scheme compromised by ÆPIC exploit.
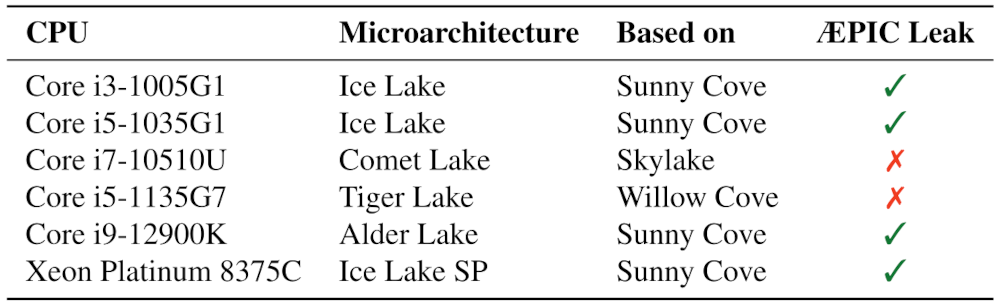
Researchers managed to crack SGX security on most 10th, 11th and 12th generation Intel processors. In a document posted by one, a table can be found that shows that this applies especially to Sunny Cove based processors.
Although it’s news what it can do when it sees its origin, the reality is that ÆPIC is not a new type of vulnerability, but rather a flaw known as an uninitialized memory read, which occurs when memory space is not cleared after the processor completes its processing. This opens the door to the leakage of old data, the processing of which is no longer necessary.
On paper, both desktops and servers are affected, but the researchers seem to be more concerned about the server situation, as services like Signal rely on SGX to ensure that the process it runs is anonymous. ÆPIC compromises SGX to the point of being able to leaking AES secret keys, RSA private keys and extracting the seal key from SGX itself for remote authentication.
Since we are dealing with a vulnerability that affects the processor, the operating system used does not matter here, and apparently virtual machines are not a solution either. ÆPIC, which is identified as CVE-2022-21233, has a severity rating of 6 out of 10, and Intel hopes to begin distributing patches to mitigate it starting Tuesday next week, while otherwise hoping to remove it. generation of processors.
SQUIP, a security flaw that requires SMT to be disabled in AMD processors
SQUIP It’s a vulnerability affects AMD’s SMT implementation, a technology that allows you to run multiple threads on a physical core (sometimes crudely called logical cores). For x86 processors, the use of SMT (HyperThreading on Intel) is currently limited to two threads per core, but other architectures are able to support more.
SQUIP is a side-channel attack that opens the door to quickly reveal a 4096-bit RSA key. The reason this affects AMD and not Intel is that processors based on the Zen architecture have separate scheduler queues for each execution unit, while Intel processors use one scheduler for the entire architecture. Separate scheduling queues for each execution unit are also present in the Apple M1 SoC, but so far there is no evidence that the Cupertino giant’s chips have been affected by the security flaw.
AMD’s SMT-enabled scheduler introduces interference into the workload, allowing it to be tracked scheduler queue contention via performance counters and unserialized timer reads in sibling threads on the same core. A person with the necessary skills and knowledge can investigate the disturbance and perform a side channel attack on the scheduler’s own queue and subsequently access sensitive data.
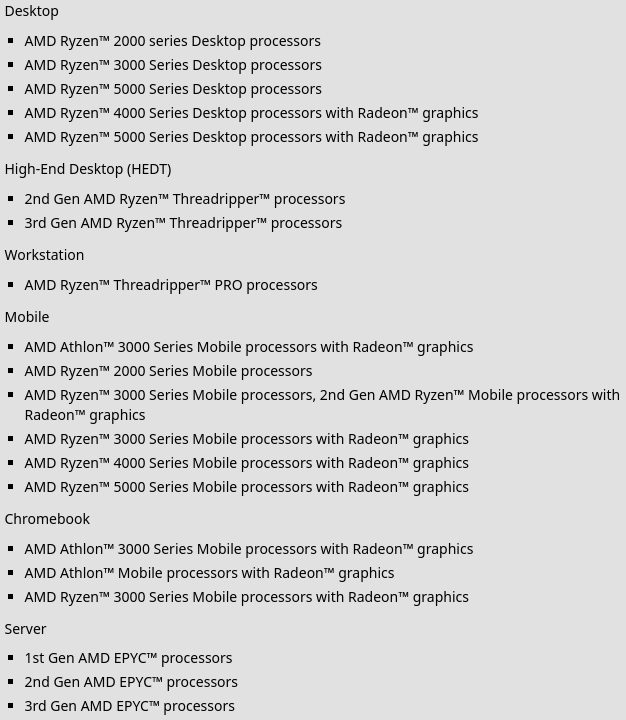
Tracked as CVE-2021-46778, SQUIP affected a large number of AMD processors: desktop Ryzen 2000 and later, Threadripper 2nd and 3rd generation, Threadripper PRO processors, notebook models from Ryzen 2000, the first three generations of Epyc, and models Athlon 3000 with Radeon graphics and Athlon Mobile with Radeon graphics. In short, most processors that are based on one of the first three generations of the Zen architecture.
AMD rated the vulnerability as moderate and “recommends that software developers use existing best practices, including constant-time algorithms, and avoid secret-dependent control flows where appropriate to help mitigate this potential vulnerability.” .
A drastic solution to avoid the SQUIP danger is to disable SMT through the motherboard settings. Although it may not seem like it, in reality many processes do not particularly affect their performance, and there are even applications that can improve their performance, including specific video games.
Are processors the new big challenge in cybersecurity?
Processor vulnerabilities have become something we have normalized as they become widespread. Interestingly, many of these issues can be resolved by turning off SMT, but this is a measure that cannot be taken in all contexts.
What is the origin of so many problems? Linus Torvalds, the creator of the Linux kernel, mentioned a few years ago the “shortcuts” that were used at the time to implement features such as speculative execution, suggesting that processor manufacturers did not consider the security implications of some of their decisions.











:quality(85)//cloudfront-us-east-1.images.arcpublishing.com/infobae/SYVEBRI7S5DKZPX44YS253RXJQ.webp)




