Google publicly asks the user to update Chrome as soon as possible due to a vulnerability actively exploited by malicious actors.
The patched version of Google Chrome is 105.0.5195.102 (at least on Windows) which fixes serious zero-day security flawtracked as CVE-2022-307, which is insufficient validation in Mojo, a collection of runtime libraries used by the Chromium browser.
Google did not provide exact information about the security flaw, and in addition stated that “access to bug details and links may be restricted until most users update to the patch“. It seems to indicate that the company made it a priority to keep the information private to avoid opening the way for cybercriminals even more, suggesting that this could be an easily exploitable vulnerability as well as a dangerous one. The bug was reported by an unidentified researcher who had already been rewarded by the search engine giant.
The lack of information leaves up in the air the possibility that Chrome isn’t the only web browser affected by the vulnerability, so if it affected the original Chromium project (which is widely used as a web browser among Linux users), that means Microsoft Edge, Opera, Vivaldi, Brave and other lesser-known applications, we therefore recommend proactively checking for updates in the following days.
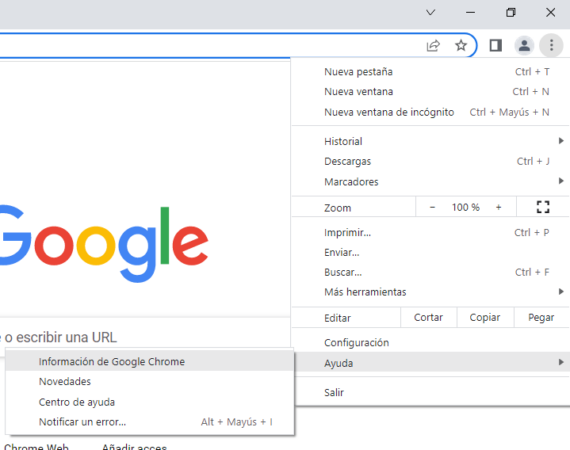
Version checking in Chrome is done from app’s main menu and go to Help > About Google Chrome. This will not only help you see the version number, but also force the update process on Windows and macOS, while on Linux you have to wait for it to arrive as a system update via Google or Google Repository. third parties such as Flathub. At least for now, Google hasn’t mentioned Android.
As we’ve said, Google’s lack of transparency on this issue leaves it up in the air as to whether the vulnerability originates in Chromium or Chrome. If you are in the former, it would be highly recommended to check for updates for the derivative of the day, be it Microsoft Edge, Opera, Brave, Vivaldi, etc.