Account theft on Steam, as with other massive gaming services, is commonplace Group-IB have detailed the latest malicious campaign that uses a phishing technique known as Browser-in-the-Browser which is gaining popularity among hackers.
This technique is an attack method that involves creating fake browser windows in an active window that pretends to be a legitimate login pop-up page for a given Internet service. The goal is steal user credentials.
Although no one is safe, as the same technique can be used against any user and service, the Steam campaign is primarily looking for professional players whose accounts can be worth a whopping $100,000. Potential victims receive direct messages on Steam inviting them to join a team for LoL, CS, Dota 2 or PUBG tournaments.
The links will lead the targets to what appears to be an organization that sponsors and organizes esports competitions. It is indeed a site controlled by attackers and according to the investigation very well done. Landing pages support 27 languages, detect the same from the victim’s browser preferences and load the correct one.
Once the victim enters their credentials, a new form asks them to enter a 2FA code. If authentication is successful, the user is redirected to a specified URL controlled by the hacker’s command and control server, usually a legitimate address to minimize the chance of the victim noticing the fraud.
at this point the victim’s credentials have already been stolen and changed passwords and email addresses to make it harder for victims to regain control of their accounts.
Stealing Steam Accounts Attention!
Attacks Browser-in-the-Browser are difficult to detect because the other url created looks legitimate because the attackers are free to display whatever they want, it’s not a browser window, it’s just a rendering. The same goes for the lock symbol on an SSL certificate, which indicates an HTTPS connection, which creates a false sense of security for victims. But like other malicious campaigns, they are all part of the same, phishing.
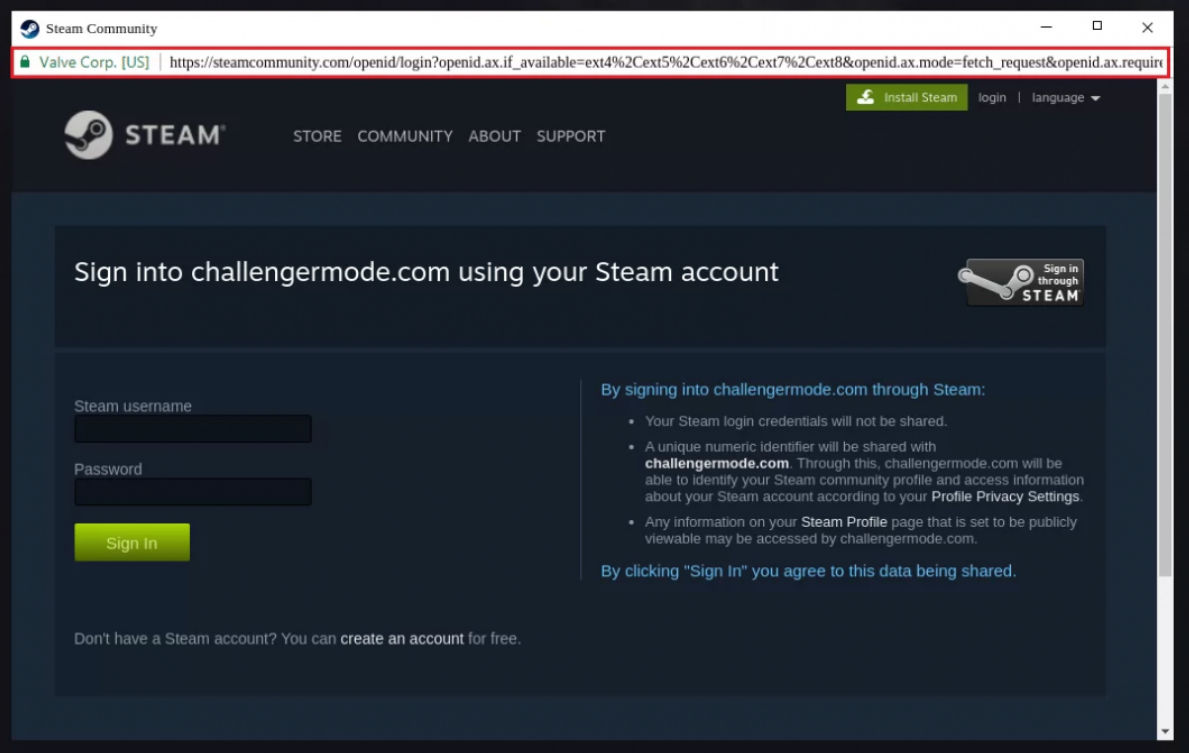
Even worse, users can drag, minimize, maximize and close the fake window, making it very difficult to detect it as an attack. Since this technique requires JavaScript, aggressively blocking JS scripts would prevent the fake login from being displayed. However, most users do not block these scripts because they would not load or prevent their favorite websites from working properly.
The solution to be safe from account theft would be before everything described and assumed beware of phishing because it is the great computer attack of our days along with ransomware. You need to know the general advice by heart, but especially with game services, be very careful with direct messages received on Steam, Discord, and other platforms, and never follow links sent by users you don’t know.















