Uber is investigating a cyber security incident following a cyber attack that could have seriously affected its business. critical infrastructure and potentially the personal data of millions of users.
According to the information available so far, an unknown attacker managed to get into the computer systems of the world’s largest mobility-as-a-service company. Screenshots shared by the cybercriminal himself show what appears to be a full access to critical Uber IT systemsincluding corporate security software and a Windows domain.
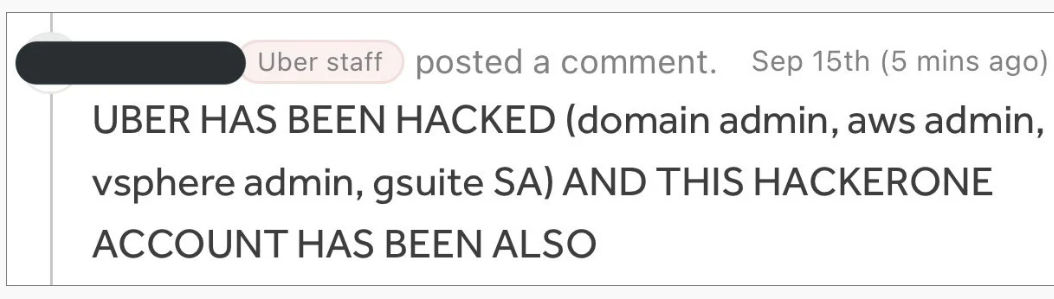
The compromised systems are broad and relevant, including the company’s Amazon Web Services console, VMware ESXi virtual machines, the Google Workspace email management panel, and the Slack server to which the hacker posted your messages.
As serious as this is, the worst for Uber may be the hack of its HackerOne bug bounty program, which allows security researchers to privately reveal vulnerabilities. If you suspect that you have gained access to all of the company’s private vulnerability records, it likely contains vulnerability reports that have not been patched, posing a serious security risk to Uber.
How Uber was cyberattacked
The New York Times, which was first to report about the cyberattack on Uber, explaining that it was carried out via social engineering against a high ranking employee and specifically by compromising your account for the business communication service Slack.
Social engineering has become a very popular technique among cybercriminals and we have seen it in recent attacks against other companies such as Twitter, MailChimp, Robinhood and Okta. The user is always the “weakest” link in the security chain and it is the principle that supports this type of computer attack.
In addition to the compromise of critical IT systems and the security bug bounty of the HackerOne program (for the stated reasons very serious), it is not excluded that the personal data of users has been compromised.
This is not the first incident of this type for Uber. In 2018, it agreed to pay $148 million for a 2016 data breach that the ride-sharing service covered up in violation of regulations. Uber’s security chief at the time was accused of covering up the breach.
On that occasion, hackers stole data from 57 million drivers and passengers, including personal information such as names, email addresses and driver’s license numbers. Uber illegally covered up the case, paid the hackers $100,000 to remove the information and asked them to sign a non-disclosure agreement. The current cyber attack appears to be even more serious, although there is no official information that we can assess. We will tell you.
“Terrible” business behavior
And related… The Guardian and the International Consortium of Investigative Journalists recently published thousands of leaked confidential Uber files and revealed that the company knowingly broke all kinds of lawsit secretly lobbied governments, withheld evidence of its operations from the police, received help from politicians and used violence against its drivers to promote business.

The overall goal was to disrupt the taxi industry in Europe to bring shared rides to cities around the world, even if they knowingly break existing regulations. Uber’s ruthless business methods were well known, but for the first time the leaked files provided a unique insider’s view of the efforts it took to achieve its goals.
Uber’s current leadership has acknowledged many of the mistakes the company made under Travis Kalanick, but has distanced itself from them. At least in computer security, they will have to make more efforts.















