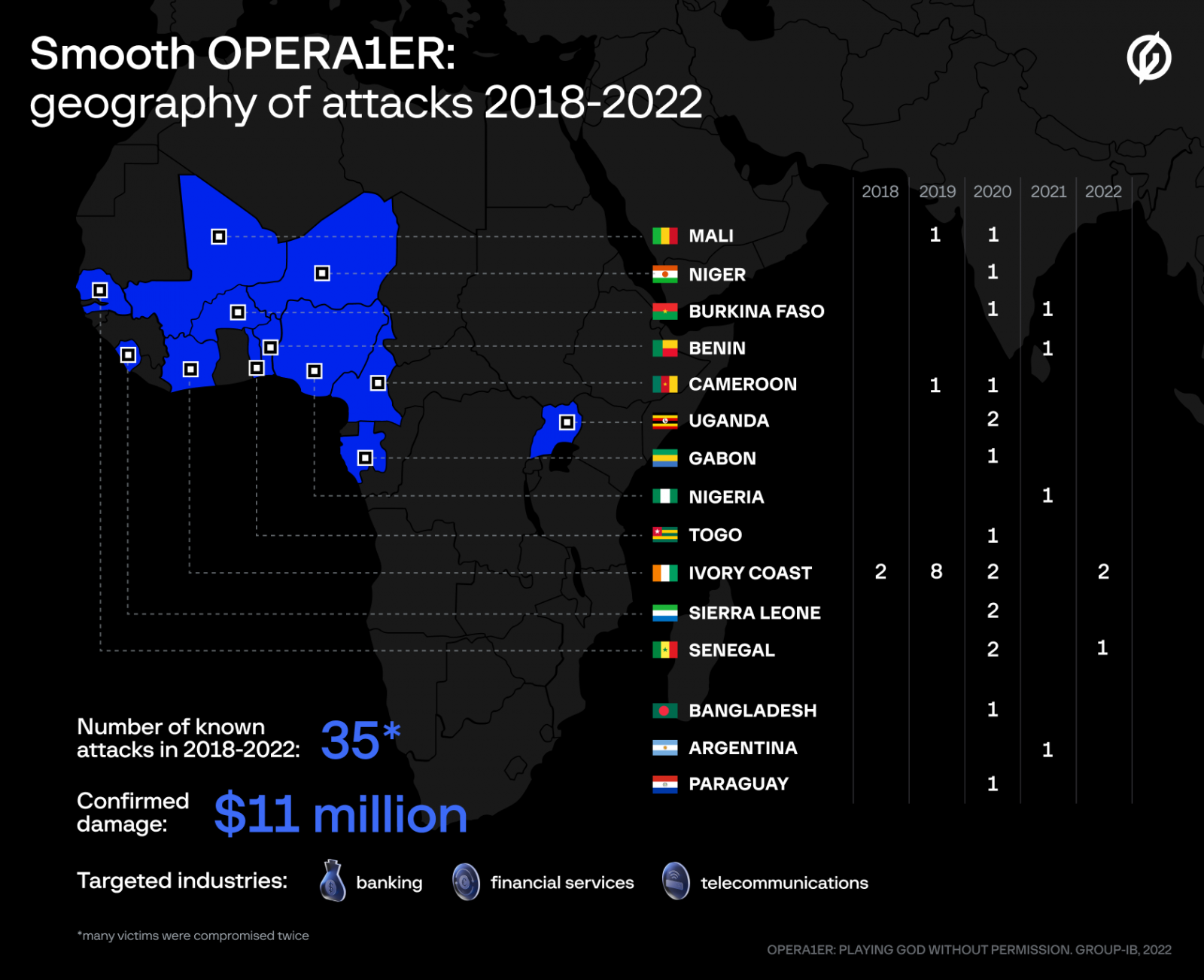
The threat group, which the researchers call OPERA1ER, has stolen at least $11 million from banks and telecommunications service providers in Africa using standard hacking tools. Between 2018 and 2022, hackers carried out more than 35 successful attacks, of which about a third were carried out in 2020.
Group-IB analysts working with CERT-CC at Orange have been monitoring OPERA1ER since 2019 and noticed that the group had changed its methods, tactics and procedures (TTP) over the past year. Worried about the possibility of losing track of the threat, the cybersecurity firm waited until the group resurfaced to issue an updated report. This year, Group-IB noticed that the hackers had become active again.
Details of the OPERA1ER attack
The hacker group consists of French-speaking members believed to operate outside of Africa. The gang hit companies in Argentina, Paraguay and Bangladesh as well as companies in Africa.
OPERA1ER relies on open source tools, malware, and frameworks like Metasploit and Cobalt Strike to compromise company servers. They gain initial access through phishing emails with popular topics such as invoices or mail delivery notifications.
Emails have attachments that offer first-stage malware, including Netwire, bitrat, venomRAT, AgentTesla, Remcos, Neutrino, BlackNET, and Venom RAT. Group-IB also says that hackers are deploying password sniffers and scavengers. According to researchers, OPERA1ER can spend three to twelve months in compromised networks, sometimes attacking the same company twice.
Researchers say that once they gain access to a victim’s network, hackers can also use the infrastructure as a mainstay for other purposes. Group-IB says the threat generates “high-quality” phishing emails written in French. In most cases, the messages impersonate the State Revenue Service or a recruitment agent from the Central Bank of West African States (BCEAO). Source