Cloudflare, many companies internet security and DDoS protection A US-based company that Today, with the increase in cyber attacks, Cloudflare has started to encounter such incidents very often in the companies it serves.
The DDoS attack, which Cloudflare discovered in a short time, was one of the largest attacks they have ever encountered. While it has similar features to typical DDoS attacks, the details of the attack, which are said to have reached gargantuan proportions, have been disclosed.
The number of requests filling the network exceeds 15 million

If the DDoS attack on an unidentified cryptocurrency platform goes undetected, the figures released today show just how large its dimensions can be. What Cloudflare Engineers Describe as the Biggest DDoS Attack They’ve Ever Experienced detected within 20 seconds and great losses were averted.
Although the attack was of great concern because of its size, it was noticed in a short time and the damage incurred was kept to a minimum. Cloudflare, the culprit worldwide Botnet representing 6,000 bots in 112 countries announced that it was carried out by The attack allegedly carried out through server providers running Java-based applications of the cryptocurrency platform. However, it is also possible that they took advantage of the lack of updates on the servers.
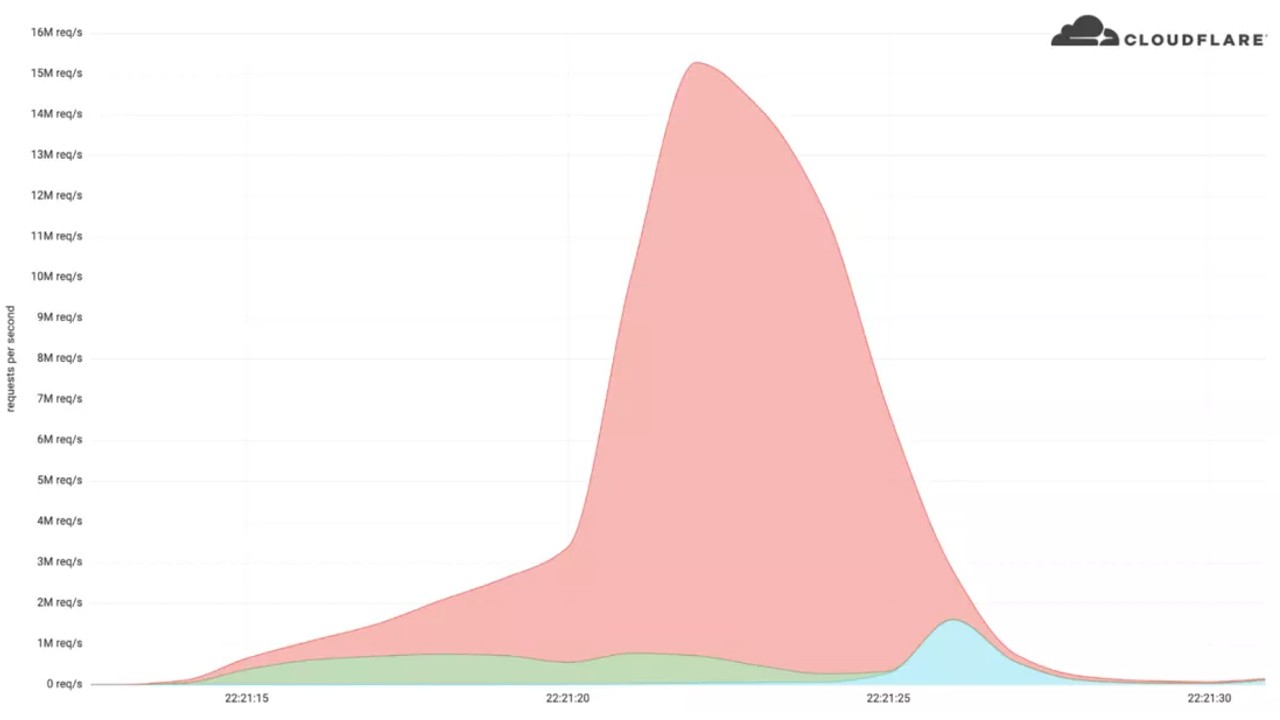
The table above shows Cloudflare’s traffic analysis. In the first seconds of the attack, between 500,000 and 1 million requests were registered and sent to the platform. In the next five seconds, these requests increase to 3 million and then to 15.3 million. reached .. After he managed to avert the attack by intervening quickly, traffic was returned to normal.
Cloudflare attacks Most come from Indonesia. and the countries that followed were Russia, Brazil, India, Colombia and the US. It is argued that instead of typical HTTP-based attacks, HTTPS-based attacks, as in this example, are much more resource intensive and the consequences can be much greater. Cloudflare engineers underline that companies should be more careful about security vulnerabilities and that updates alongside fixes should not be interrupted.















