Cybersecurity training for employees: how do you go about it?
- September 5, 2023
- 0
Educating your employees on how to recognize and avoid cyber attacks is vital to keeping your organization safe. But how do you start? We discuss some best practices
Educating your employees on how to recognize and avoid cyber attacks is vital to keeping your organization safe. But how do you start? We discuss some best practices


Educating your employees on how to recognize and avoid cyber attacks is vital to keeping your organization safe. But how do you start? We discuss some best practices and tools that can help you with this.
The human factor should not be underestimated when it comes to cyber security. In 2022, the WEF calculated that 95 percent of cyber incidents were due to human error. The exact percentage is disputed among statisticians, but employees are generally considered to be the weakest link in corporate security.
You can invest as much as you like in virus scanners and firewalls, but if your employees keep clicking on suspicious links, they’re useless. Employees are not always very aware of their responsibility and the consequences of unsafe digital behavior. Social engineering, a collection of attack techniques that attempt to exploit human behavior, including phishing, is increasing every year.
However, there is nothing that cannot be learned, and cybersecurity is all about learning how to use technology safely. Nowadays there are many (online) courses that you can let your employees take part in, but without guidance they rarely achieve the desired effect. Cybersecurity training is a process that takes time and effort.
Phishing is and remains the proven recipe for attackers to penetrate companies. Although the danger is now well known, people fall into the trap every day. Because the phishing e-mails are getting better and more realistic.
Almost nobody falls for an email from a Nigerian prince who leaves you his entire legacy on condition that you transfer a small amount of money. But an email that appears to be coming from your boss or co-worker and is about a project you’re working on makes you second-guess. Using AI only makes phishing emails look more realistic, which also increases the need to train your employees to recognize phishing.
There are still different degrees of phishing. The more personal information an attacker can find, the more personal they can make the email and the more likely the victim is to believe it. This also depends on how much effort the hacker is willing to put into their campaign. Security company Hornetsecurity distinguishes seven levels of phishing, listed below with the preparation time required for the hacker for each type.
| level | What? | preparation time |
| 1 | Bulk Phishing: Deceptive bulk emails sent to random addresses. A case in point is a fake email impersonating Bpost saying a package is on its way. | +/- 15 minutes |
| 2 | CEO Fraud: An email purporting to come from a senior manager within the organization. | +/- 1 hour |
| 3 | Spear phishing emails containing public information about the company. | +/- 2 hours |
| 4 | Spear phishing emails directly related to the victim’s department or role, or emails from direct colleagues/supervisors. | +/- 4 hours |
| 5 | “Fake” email from a business partner who hasn’t activated anti-spoof protection or whose account has been compromised. | +/- 6 hours |
| 6 | Email from a personal contact in response to a previous conversation. Often with a hacked email account. | +/- 12 hours |
| 7 | Spear phishing email related to something the recipient is working on, such as a status update on an ongoing project. | More than 20 hours |
Source: Hornet Security
The most important skills employees need to learn are recognizing phishing emails, suspicious email addresses and/or links. There are many indicators that you can look at, which we explain in detail in this guide. But you don’t hammer that into your employees after one mandatory course a year, especially not those who are less digitally savvy.
Provide ongoing education and training to maintain knowledge and keep employees updated on evolving threats. But be careful not to overdo it: hitting employees with warnings or a reprimanding finger is counterproductive. The trick is to see employees as the first line of defense rather than a risk. A firewall, but one made of flesh and blood.
As is often the case with cyber security training, you will get the most progress with a data-driven approach. Create clear KPIs against which to test employee progress. Hornetsecurity developed this Employee Safety Index (ESI)a value that expresses how well someone performs in comparison to the “exemplary employee”.
A score of 90 or more on this scale represents exemplary behavior. If your score is eighty, then you have acted negligently twice as often (e.g. clicked on a phishing link), if your score is seventy three times as often. A perfect report is not realistic, people make mistakes, but when the score falls below seventy, additional training is badly needed.
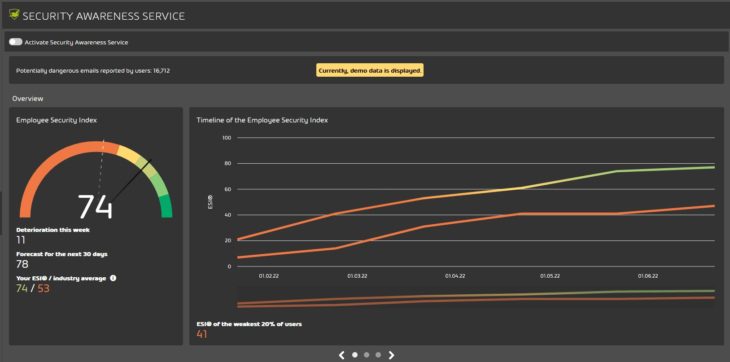
Hornetsecurity’s scale also highlights the importance of repeat training. An analysis of 1.7 million phishing simulations shows that with enough repetition, the average employee can increase their score by 30 points after 12 months. But a month’s break and the score drops by five points again. After four months without training, the drop is more than thirty points and it’s time to start over.
Cybersecurity is a matter of repetition, but numerous warnings work against the grain. Don’t think of your people as a risk, think of them as the first line of defense.
The content of the training sessions is just as important as the frequency. To engage employees, the content of the courses should also be relevant to them. Make sure the simulation exercises are tailored to each role, responsibility, and potential risk.
Developing and implementing a personal training program for each employee takes a lot of time and resources. This task often falls on the shoulders of already overburdened IT teams. This is where digital training platforms like the come in Hornet Security Awareness Service practical.
The Security Awareness Service automates the entire training process. The awareness engine automatically creates a schedule for the user: how much training each needs and what content is most relevant. The employee then receives e-mails at regular intervals that simulate a phishing attempt, although of course the employees must not know when they will arrive. That too is all automated.
You can then follow how everyone is doing on the Awareness Dashboard. It not only measures how often the e-mail is clicked, but also how often a phishing e-mail was reported. Based on the behavior of the employee and the level of difficulty of the exercises, the previously discussed ESI score is created for each employee. This can be further monitored over time to tailor the training program.
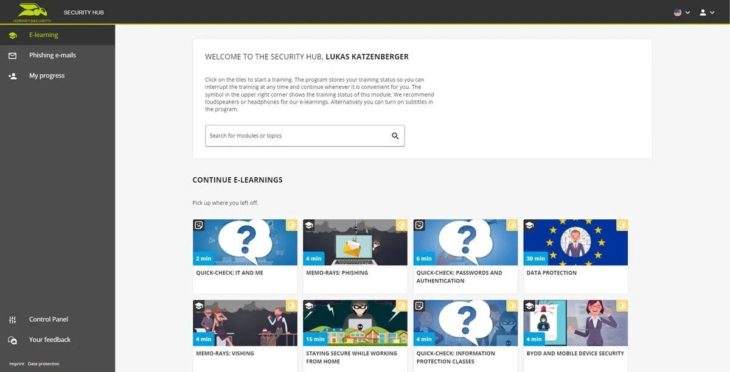
The Security Awareness Service encompasses more than just phishing. Employees also have access to tutorials and videos through their personal dashboard, which they can also use to learn how to securely secure their accounts, emails, etc. They can also monitor their personal progress in the dashboard.
This method increases employee engagement. You can go through the tutorials anytime, anywhere and only get exercises that are relevant to you. Cybersecurity training doesn’t always have to feel like a required class.
In order to motivate employees, the training content should be relevant to them.
This editorial contribution was created in cooperation with Hornetsecurity. For more information on the company’s Security Awareness Service and other security solutions, click here.
Source: IT Daily
As an experienced journalist and author, Mary has been reporting on the latest news and trends for over 5 years. With a passion for uncovering the stories behind the headlines, Mary has earned a reputation as a trusted voice in the world of journalism. Her writing style is insightful, engaging and thought-provoking, as she takes a deep dive into the most pressing issues of our time.