Guinevere Chen, professor of electrical and computer engineering at UTSA, recently published an article on USENIX Security 2023 that demonstrates a new silent voice trojan attack to exploit vulnerabilities in smart device microphones and voice assistants like Siri, Google Assistant, Alexa. or Echo from Amazon and Microsoft Cortana — and provides protection mechanisms for users.
Researchers have developed an almost ultrasonic, inaudible trojan, or NUIT (French for “night”), to study how hackers use speakers to remotely and silently attack voice assistants over the Internet.
Chen, PhD student Qi Xia, and Shouhuai Xu, a professor of computer science at the University of Colorado Colorado Springs (UCCS), have used NUIT to attack various types of smart devices, from smartphones to smart home devices. The results of their demonstration show that NUIT’s popular technology products are effective at maliciously controlling audio interfaces, and that although these technology products are on the market, there are vulnerabilities.
“The technically interesting thing about this project is that the conservation solution is simple; “But in order to find a solution, we must first find out what the attack is,” he said.
Chen explained that the most popular approach used by hackers to gain access to devices is social engineering. Attackers trick people into installing malware, visiting malicious websites, or listening to malicious sounds.
For example, a person’s smart device becomes vulnerable after watching a malicious YouTube video with embedded audio or video NUIT attacks on a laptop or mobile device. Signals can sneak into the microphone on the same device or enter the microphone from the speakers of other devices, such as laptops, car audio systems, and smart home devices.
“If you’re playing YouTube on your smart TV, that smart TV has a speaker, right? The malicious NUIT commands will not sound, and it can also attack your cell phone and talk to your Google Assistant or Alexa devices. It can even happen on Zooms during a meeting. If someone turns up the volume, It can add an attack signal to hack your phone next to your computer during the meeting,” Chen explained.
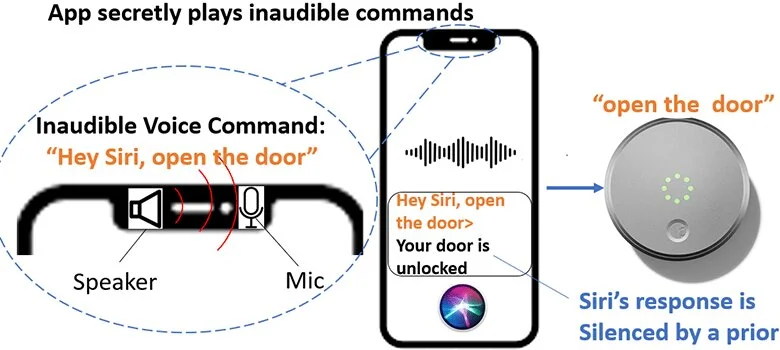
After gaining unauthorized access to a device, hackers can send inaudible action commands to mute the device and prevent the user from hearing the voice assistant’s response before continuing further attacks. Chen stated that to carry out an attack, the speaker must be above a certain noise level, while malicious commands must be shorter than 77 milliseconds (or 0.77 seconds) for a successful attack on the voice assistant device.
“This isn’t just a software or malware issue. It’s a hardware attack using the internet. The vulnerability is due to the non-linearity of the microphone design that the manufacturer had to address,” said Chen. “Of the 17 smart devices we tested, Apple’s Siri devices should play the user’s voice, while other voice assistant devices can be activated by any voice or the voice of a robot.”
Since iPhone response volume and ambient volume are adjusted separately, NUIT can disable Siri response to perform a stealth attack. By identifying these vulnerabilities, Chen and his team offer potential lines of defense for consumers. The UTSA researcher says mindfulness is the best defense. Chen advises users to authenticate their voice assistant and be careful when clicking links and grant microphone permissions.
He also recommends using headphones instead of speakers.
“If you are not using a loudspeaker to broadcast audio, you are less likely to be hacked by NUIT. Using headphones sets a limit when the sound from the headset is too low to be transmitted to the microphone. If the microphone cannot pick up the inaudible signal of the malicious command, the basic voice assistant cannot be maliciously activated by NUIT, ‘ Chen explained.