Security researchers can now access Microsoft Defender’s database, including file hashes and URLs.
Defender Threat Intelligence enables researchers to perform both static and dynamic analysis of files and URLs both inside and outside of a Microsoft environment. This dual approach makes it possible to identify and classify potential dangers more quickly.
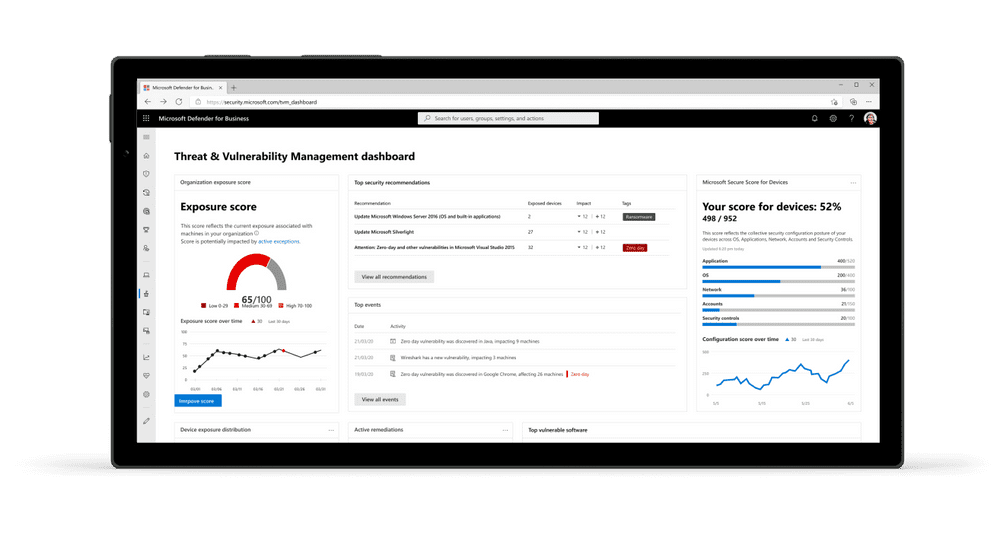
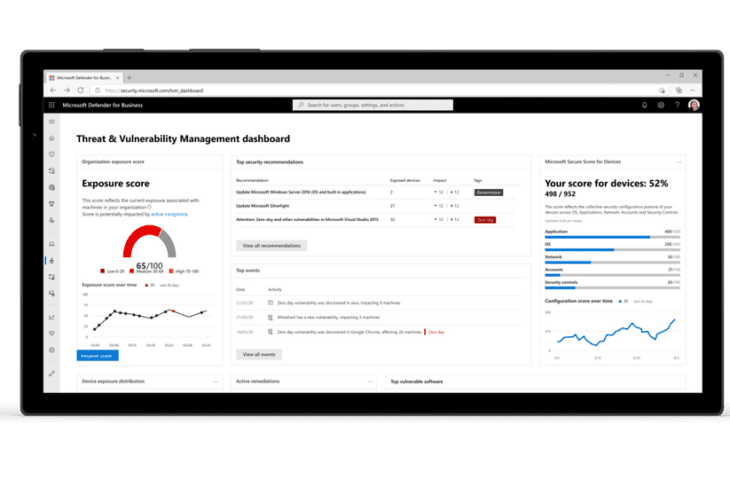
According to Microsoft, DNS data, WHOIS information, malware, and SSL certificates provide important context for analysis, but these repositories are scattered and don’t share the same data structure. This makes it difficult for researchers to have all the relevant data available for a correct analysis.
With Defender TI, Microsoft wants to bundle this information and add its own value, which Google has been doing with VirusTotal for years. Within Defender TI, researchers can type a hash or URL into the search bar and Microsoft will return a result. At first glance, it’s short with the reputation score and basic info, but below that Eventsfind out which rules were triggered to justify the displayed score.
The Defender TI database may be of interest to security researchers as a complement to other tools. As a software giant, Microsoft collects a huge amount of data related to malware signals and other threats to security products and Azure data. Defender TI is the result of last year’s acquisition of RiskIQ and analyzes 43,000 billion signals daily.